
Features
Technology
Finding the heart of cybercrime in the perimeter-less landscape: Enter NC3
Keynote address from the RCMP’s National Cybercrime Coordination Unit (NC3) at Toronto Cybersecurity Conference highlights the aim to protect Canadian citizens from evolving threats
November 15, 2019 By Alexander Lomasney and Michael Hiskey
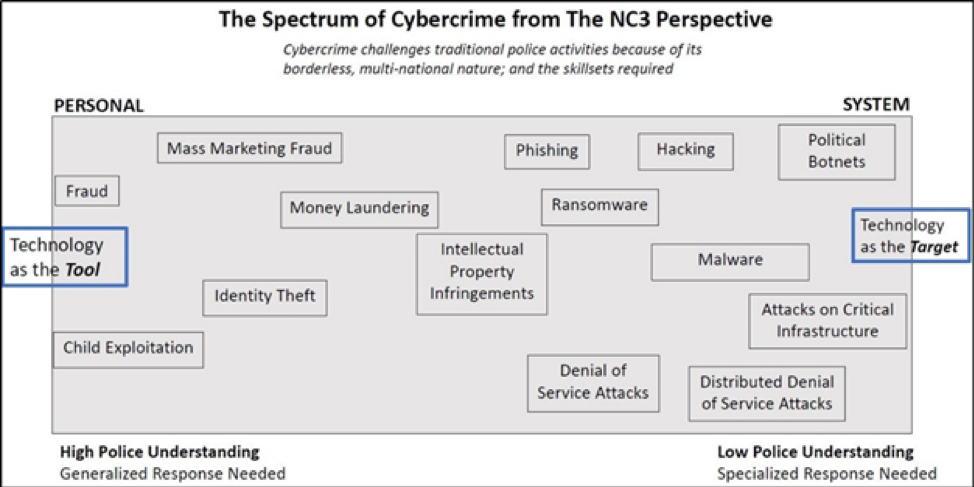 Image submitted by authors.
Image submitted by authors. This article details an October 2019 briefing from Chris Lynam, DG-NC3, Director General, National Cybercrime Coordination Unit, RCMP, during the Data Connectors Cybersecurity Strategies Conference in Toronto.
Threats evolve over time, as do the police forces facing down these threats.
The Royal Canadian Mounted Police (RCMP) was formed 100 years ago on Feb. 1, 1920. The lineage of the RCMP traces back to the North-West Mounted Police (NWMP), established in 1873 by Canada’s first Prime Minister Sir John A. Macdonald.
The mission of the NWMP in 1873 was to maintain order across the North-West Territories, an area that is today Western Canada. The force countered macro-threats to Canadian sovereignty and individual threats to citizen-ranchers.
Back to present times, Chris Lynam serves as the director general of the RCMP’s National Cybercrime Coordination Unit (NC3) in Ottawa. Lynam is leading the RCMP’s response to rapidly evolving threats, namely those perpetrated in cyberspace. NC3, as the NWMP was in the past, is tasked with responding to threats to sovereignty, businesses and Canadian citizens.
At the Data Connectors Cybersecurity Strategies Conference last month, Lynam delivered a keynote address focused on introducing the audience to NC3. He began by explaining that traditional policing was border-based, with physical jurisdictions making far away threats minimally impactful on society.
“Today, with the emergence of cybercrime: the suspect, the victim and the evidence/data are all segmented and physical boundaries matter much less,” he said.
Photo: Michael Hiskey
For many, software-as-a-service (SaaS) is a familiar idea; ‘cybercrime as a service’ is a similar concept. Criminals operating in cyberspace don’t need to be the ones who develop an exploit, they can outsource nearly every aspect of an attack.
A far cry from the stereotype of a solitary hacker in a basement, criminal elements have organized and refined their digital weapons over the last decade. As we all know, the ease of retaining anonymity through digital crime is a challenge for law enforcement and an incentive for criminal actors.
Physically robbing a bank creates an evidence trail with security cameras, licence plate databases, gait analysis, facial recognition, DNA, witness accounts, ballistic forensics, and a series of other CSI-type tools. Digitally robbing a target with the correct tools and tactics can be done with near-perfect anonymity; attribution is extremely difficult, especially for local police forces lacking technical resources.
Criminal enterprises have taken note of this, and many have formed corporate-style enterprises with the goal of perpetrating crimes in the digital domain. In fact, many have shifted their actions from the physical to the digital domain. The simplified organization chart of a digital criminal organization consists of developers; marketing teams (focused on propagating the exploit); leadership; money handlers, and; OPSEC (operational security) units. These units are well funded, act with impunity and have grown considerably larger in the last 10 years.
Enter NC3, part of Canada’s response to malicious actors in the digital domain. NC3 is a National Police Service, meaning its aim is to support all branches of law enforcement.
NC3 enables Canadian police organizations to pursue cybercriminals. To collectively advance this cause, some police units throughout the country have specialized cybercrime units. Most often, NC3 provides technical advice, tools, techniques and other forms of guidance. They aim to produce Cybercrime Intelligence Reports related to both new and existing threats.
NC3 is not focused on policing one jurisdiction, rather it carries a national mandate with international liaison capabilities. This mandate is to enable and empower Canadian law enforcement to better address cybercrime to reduce the threat, victimization and impact on Canadians. The focus is on technically sophisticated and high-impact cybercrimes.
NC3’s role is to:
- Work with law enforcement to co-ordinate and deconflict cyber investigations in Canada and with international partners.
- Provide digital investigative advice and guidance to specialist police units across Canada.
- Produce actionable intelligence for Canadian police (cybercrime intelligence).
- Establish a new national public mechanism/portal for Canadian SMBs to report cybercrimes to police.
Lynam explained NC3’s main focus is on the ‘technology as the target’ crimes; though they will also target ‘technology as the tool’ crimes if these crimes are deemed to be of high social or monetary impact on Canadian interests.
Examples of ‘technology as the target’ crimes are exploits targeting a system—attacks on critical infrastructure like hydro-dams and nuclear power plants. ‘Technology as the tool’ crimes see criminal actors focus on child exploitation, fraud and money laundering. Interestingly for Canadian businesses, ransomware, intellectual property theft, phishing and denial of service attacks all fall somewhere in the middle of this spectrum.
Ultimately, NC3 targets the head of the snake; “We can only build the perimeter so hard; we need to focus our efforts on attacks and the people behind cybercrimes,” Lynam explained.
At present, NC3 is acting in a pathfinder capacity: diving into the threat landscape as an advance force, bolstering existing forces with refined intelligence and guidance, liaising with multi-national partners, prioritizing threats, and deconflicting with neighbouring police forces.
“We can’t arrest our way out of this problem,” Lynam said, as he cited the challenges, as well as the opportunities for his organization to be helpful and extend investigations. He also noted that while other countries have had dedicated units working for some time, NC3 has the benefit of learning from those organization and preparing for modern threats.
Simple as it may be to become overwhelmed by the nature of new threats, Canadian society is counting on units like NC3 to look back to its roots: to understand the threats of today and to counter them while ensuring the defense of Canadian interests.
Alexander Lomasney is the manager of information security at Cyber724 and Michael Hiskey is the chief strategy officer at Avanan, a cloud email security platform that pioneered and patented a new approach to prevent sophisticated attacks.
Print this page